Knowledge base article
Recover your hacked WordPress website
This article will teach you how to restore your hacked WordPress website
If you are reading this page you are most likely, most unfortunately, hacked! Thankfully its relatively straight forward to restore your website to its former glory.
To learn about common causes for a website becoming hacked, please read our guide about common vulnerabilities which also includes recommendations for prevention.
- Firstly, if your website is redirecting to a fraud/spam website when visiting the domain in your browser, it's likely your database has been injected with the fraudulent domain name, if you are experiencing this redirect issue, lets start by checking the site_url is set correctly in the database.
To check and/or update the site_url, login to cPanel and navigate to the phpMyAdmin function. You will see your hosted databases on the left hand side of phpMyAdmin, select your database to view the tables (if you don't know which one is your live site, please check the database name stated in the sites wp-config.php file).
Now you're viewing the database tables, select the table labelled wp_options. At the top of the wp_options table take note of the top two rows, siteurl and home. These fields dictate the domain name the application uses, please check whether these are set to use the correct domain name, if not you can click in the text field to update the domain name.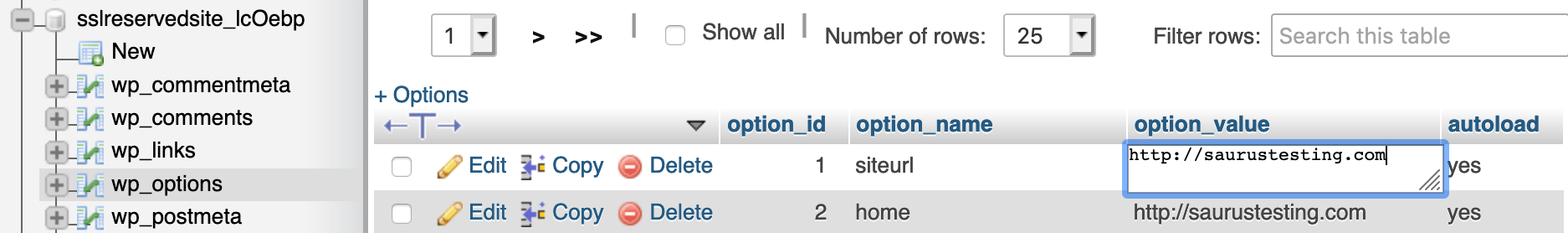
Now check if you can access the website again, if so- please continue to step 3- if the website is still appearing compromised, please continue to step 2. - We need to reinstall WordPress core to ensure the application files are "clean" (you can process this step via WordPress dashboards automated update tools if you are unable).
If you are unable to access WordPress dashboard, follow the below steps to reinstall WordPress manually
2a. SSH onto your hosting server. Replace the username and server field with your cPanel username and the name of your server. You can find these details in your Welcome to Serversaurus Business Hosting email. Enter your password at the prompt to log in.ssh username@server.serversaurus.com.au
2b. Using the wget command, we will download the latest WordPress version into our current directory.
wget http://wordpress.org/latest.tar.gz
Now to extract the contents of the latest.tar.gz file type the command:
tar xfz latest.tar.gz
2c. Change into the directory where your current WordPress site is installed.Note: This can differ depending on your setup, if these updates are for your primary website WordPress will most likely be installed under public_html.
To change into your public_html directory type and enter:
cd public_html
If you are reinstalling WordPress under an addon domain, navigate to the addon domain's home directory using the below command:
cd yourdomainname.com
2d. Now we want to copy the files/directories which are unique to your website and move them into the directory with your fresh WordPress install overwriting default directories or files that were included in the installation.
Use the below command to recursively copy your unique website files:
cp -r wp-content/ wp-config.php .htaccess ~/wordpress
2e. Next we'll remove the existing WordPress installation from the current directory
rm -fr ./*
2f. The final step is to move the new WordPress files with your content into the current directory.
mv ~/wordpress/* .
2h. Now let's tidy up after ourselves, we no longer need the WordPress directory or the latest.tar.gz file, to remove these items, issue the following command:
rm -f ~/latest.tar.gz ~/wordpress/ - Login to WordPress dashboard as before, and install WordFence (if you have not already). Then immediately run the WordFence scan, the scan will identify whether there are further compromised files and offers a tool to remove the compromised file/s, needless to say, use the tool to remove any compromised files until you receive a 100% clean scan result.
This step is important, as although you have reinstalled WordPress core, it's possible plugin or theme files could have malicious code which was not "cleaned" when reinstalling WordPress core files. - Update all WordPress user passwords!!!
You website should now be completely clean of malicious code (wippee!). If you want to take further precautions to prevent becoming hacked in the future, please complete our recommendations in our WordPress security and management guide, and for more advanced recommendations, please refer to our guide about securing a WordPress installation.
Last updated November 30, 2023